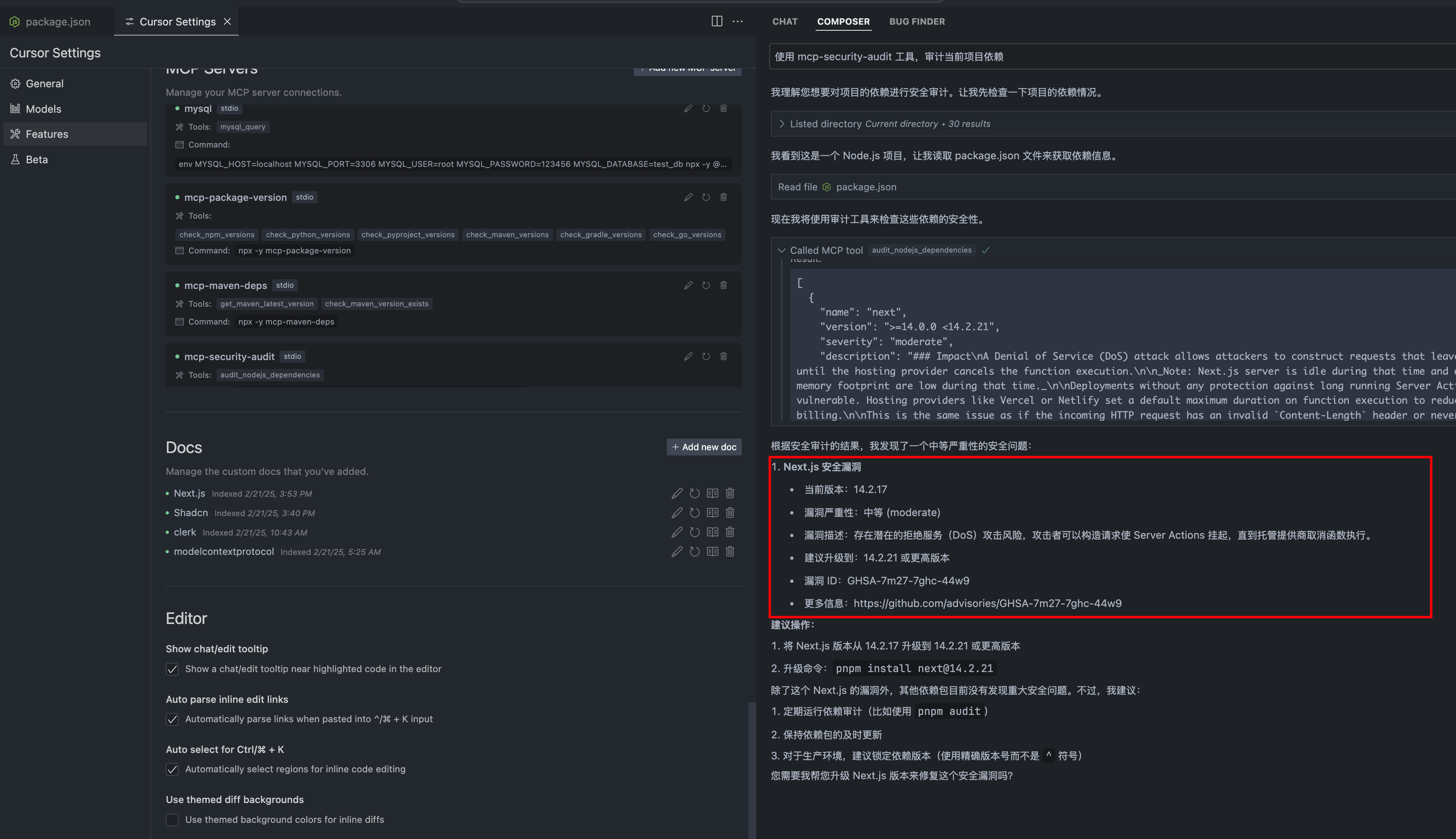
安全审计工具
一个强大的MCP(模型上下文协议)服务器,用于审计npm包依赖的安全漏洞。集成了远程npm注册表,实现实时安全检查。
概览
什么是 MCP 安全审计?
MCP 安全审计是一个强大的工具,旨在审计 npm 包依赖的安全漏洞。它利用模型上下文协议(MCP)确保开发人员能够通过识别依赖中的潜在风险来维护安全的应用程序。该工具与远程 npm 注册表无缝集成,允许实时安全检查,并为开发人员提供有关其包的安全状态的即时反馈。
MCP 安全审计的特点
- 实时安全检查:与远程 npm 注册表的集成使得对包依赖进行即时安全评估成为可能。
- 综合漏洞报告:MCP 安全审计提供关于识别到的漏洞的详细报告,包括严重性级别和建议的行动。
- 用户友好的界面:该工具以可用性为设计理念,使开发人员能够轻松浏览和理解其项目的安全状态。
- 开源:作为一个公共模板,开发人员可以为其改进做出贡献,并根据自己的需求进行定制。
- 社区支持:拥有活跃的用户和贡献者社区,开发人员可以寻求帮助并分享有关安全实践的见解。
如何使用 MCP 安全审计
-
安装:首先通过 npm 安装 MCP 安全审计工具。使用以下命令:
npm install mcp-security-audit -
运行审计:安装完成后,导航到您的项目目录并运行审计命令:
mcp-security-audit -
审查报告:审计完成后,查看生成的报告。它将列出所有发现的漏洞,并按严重性分类。
-
采取行动:按照报告中提供的建议来解决漏洞。这可能包括更新包、删除未使用的依赖或应用补丁。
-
持续监控:定期运行审计作为开发工作流程的一部分,以确保持续的安全合规性。
常见问题解答
MCP 安全审计可以检测哪些类型的漏洞?
MCP 安全审计可以检测广泛的漏洞,包括过时的包、已知的安全缺陷和您 npm 依赖中的潜在利用。
MCP 安全审计是免费使用的吗?
是的,MCP 安全审计是一个开源工具,免费使用。开发人员也可以为其开发和改进做出贡献。
我应该多久运行一次审计?
建议定期运行审计,特别是在添加新依赖或更新现有依赖后。将其集成到您的 CI/CD 流程中可以帮助维护安全标准。
我可以自定义审计报告吗?
可以,该工具允许根据您项目的特定需求自定义报告。您可以修改输出格式和报告中包含的详细程度。
我在哪里可以找到有关 MCP 安全审计的更多信息?
有关更多详细信息、文档和社区支持,请访问官方网站 mcpdirs.com。
详情
…
Server配置
{
"mcpServers": {
"mcp-security-audit": {
"command": "docker",
"args": [
"run",
"-i",
"--rm",
"ghcr.io/metorial/mcp-container--qianniuspace--mcp-security-audit--mcp-security-audit",
"node ./build/index.js"
],
"env": {}
}
}
}