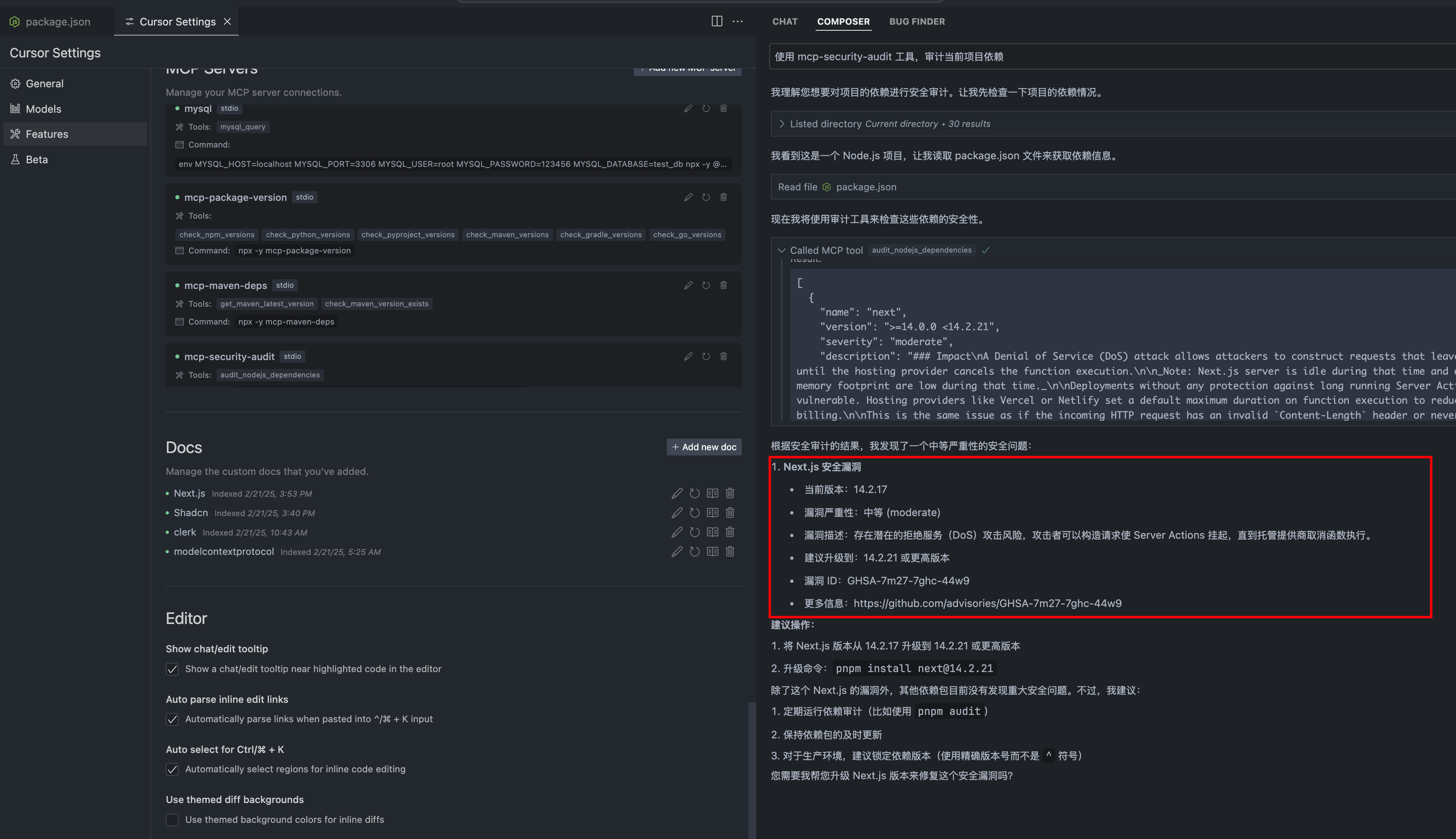
Инструмент аудита безопасности
Мощный сервер MCP (Протокол Контекста Модели), который проверяет зависимости npm пакетов на наличие уязвимостей в безопасности. Создан с интеграцией удаленного реестра npm для проверки безопасности в реальном времени.
Обзор
Что такое аудит безопасности MCP?
Аудит безопасности MCP — это мощный инструмент, предназначенный для проверки зависимостей пакетов npm на наличие уязвимостей безопасности. Он использует Протокол Модельного Контекста (MCP), чтобы обеспечить разработчиков возможностью поддерживать безопасные приложения, выявляя потенциальные риски в их зависимостях. Инструмент бесшовно интегрируется с удаленными реестрами npm, позволяя проводить проверки безопасности в реальном времени и предоставляя разработчикам немедленную обратную связь о статусе безопасности их пакетов.
Особенности аудита безопасности MCP
- Проверки безопасности в реальном времени: Интеграция с удаленными реестрами npm позволяет мгновенно оценивать безопасность зависимостей пакетов.
- Полные отчеты о уязвимостях: Аудит безопасности MCP предоставляет подробные отчеты о выявленных уязвимостях, включая уровни серьезности и рекомендуемые действия.
- Удобный интерфейс: Инструмент разработан с учетом удобства использования, что делает его простым для навигации и понимания статуса безопасности проектов разработчиков.
- Открытый исходный код: Будучи публичным шаблоном, разработчики могут вносить свой вклад в его улучшение и настраивать его в соответствии со своими потребностями.
- Поддержка сообщества: С активным сообществом пользователей и участников разработчики могут искать помощь и делиться мнениями по вопросам практик безопасности.
Как использовать аудит безопасности MCP
-
Установка: Начните с установки инструмента аудита безопасности MCP через npm. Используйте команду:
npm install mcp-security-audit -
Запуск аудита: После установки перейдите в каталог вашего проекта и выполните команду аудита:
mcp-security-audit -
Просмотр отчета: После завершения аудита просмотрите сгенерированный отчет. Он перечислит все найденные уязвимости, классифицированные по уровням серьезности.
-
Принятие мер: Следуйте рекомендациям, указанным в отчете, чтобы устранить уязвимости. Это может включать обновление пакетов, удаление неиспользуемых зависимостей или применение патчей.
-
Непрерывный мониторинг: Регулярно запускайте аудит как часть вашего рабочего процесса разработки, чтобы обеспечить постоянное соблюдение стандартов безопасности.
Часто задаваемые вопросы
Какие типы уязвимостей может обнаружить аудит безопасности MCP?
Аудит безопасности MCP может обнаружить широкий спектр уязвимостей, включая устаревшие пакеты, известные проблемы безопасности и потенциальные эксплойты в ваших зависимостях npm.
Бесплатен ли аудит безопасности MCP?
Да, аудит безопасности MCP — это инструмент с открытым исходным кодом и его можно использовать бесплатно. Разработчики также могут вносить свой вклад в его разработку и улучшение.
Как часто я должен запускать аудит?
Рекомендуется регулярно запускать аудит, особенно после добавления новых зависимостей или обновления существующих. Интеграция его в ваш CI/CD процесс может помочь поддерживать стандарты безопасности.
Могу ли я настроить отчеты аудита?
Да, инструмент позволяет настраивать отчеты в соответствии с конкретными потребностями вашего проекта. Вы можете изменить формат вывода и уровень детализации, включаемый в отчеты.
Где я могу найти больше информации об аудите безопасности MCP?
Для получения дополнительной информации, документации и поддержки сообщества посетите официальный сайт по адресу mcpdirs.com.
Деталь
Конфигурация сервера
{
"mcpServers": {
"mcp-security-audit": {
"command": "docker",
"args": [
"run",
"-i",
"--rm",
"ghcr.io/metorial/mcp-container--qianniuspace--mcp-security-audit--mcp-security-audit",
"node ./build/index.js"
],
"env": {}
}
}
}Информация о проекте
Инструмент аудита бе... Альтернатива
В качестве альтернативы Инструмент аудита бе... которую вы можете рассмотреть, мы предлагаем сайты, разделённые по категориям.
Приватный MCP-прокси, который интеллектуально псевдонимизирует ЛИЧНЫЕ ДАННЫЕ в реальном времени до того, как данные достигнут внешних поставщиков ИИ, сохраняя семантические связи для точного анализа.